Introduction
Inventory management systems have evolved from simple spreadsheets into complex, integrated platforms that handle real-time stock tracking, supplier coordination, warehouse automation, and analytics. In today’s digital-first world, SaaS-based inventory platforms must not only scale to support thousands of clients but also maintain strict data isolation, security, and availability. This is where multi-tenancy becomes a game changer.
This architecture guide explores how to design a robust, scalable, and secure multi-tenant inventory management platform on AWS. The system is built for SaaS vendors serving multiple retail, manufacturing, or logistics businesses, each with its own users, warehouses, catalogs, and workflows.
Modern businesses demand real-time visibility, high availability, and operational agility. This means the backend must scale seamlessly, support custom logic per tenant, and integrate with external ERP, shipping, and payment systems. Tenants expect configurable business rules, role-based access, and usage analytics — all without compromising on performance.
Multi-tenancy adds another layer of complexity. It requires careful design around tenancy models (pooled vs. isolated), shared infrastructure, security boundaries, and scaling policies. And when you mix that with inventory-specific requirements — like stock thresholds, SKU versioning, purchase orders, and warehouse zone mapping — things can get hairy fast.
This guide breaks down how to build such a platform from the ground up using AWS-native services and battle-tested design principles. We’ll dive deep into tenancy patterns, data partitioning, API architecture, deployment strategies, and scalability levers — with real-world scenarios and implementation insights baked in.
If you’re building a SaaS inventory system, migrating a legacy platform, or simply rearchitecting for scale, this is the playbook.
System Requirements
Functional Requirements
- Multi-tenancy: Support multiple tenant organizations with logical data isolation and configurable features.
- Inventory Management: Track products, SKUs, stock levels, batch numbers, expiration dates, and locations (warehouse, zone, bin).
- Inbound & Outbound Logistics: Manage purchase orders, receiving, sales orders, and fulfillment workflows.
- Role-Based Access Control (RBAC): Define granular permissions for users (e.g., warehouse manager, purchasing agent, admin).
- Audit Logging: Capture and store a complete history of stock movements, user actions, and API calls.
- API-First: Expose all operations via REST/GraphQL APIs for integration with ERPs, shipping providers, and e-commerce frontends.
- Real-Time Notifications: Trigger alerts for stock thresholds, order status changes, and system events.
- Reporting & Analytics: Provide dashboards, KPIs (e.g., stock turns, fill rate), and exportable reports for each tenant.
Non-Functional Requirements
- Scalability: Must scale horizontally to handle variable tenant workloads, seasonal spikes, and data volume growth.
- High Availability: Target 99.99% uptime SLA with failover, backups, and resilient architecture.
- Security: Enforce strict tenant data isolation, encrypted storage, secure APIs, and per-tenant access policies.
- Observability: Provide centralized logging, metrics, and distributed tracing across tenant boundaries.
- Configurability: Allow tenants to customize workflows, business rules, and field-level configurations without affecting others.
- Cost Efficiency: Optimize resource usage through shared services where possible without compromising isolation or performance.
- Global Reach: Support multi-region deployments for global clients with data residency considerations.
Constraints
- Cloud-Native: Must use AWS-managed services where feasible to reduce operational overhead.
- Zero Downtime Deployments: All updates must support rolling or blue-green strategies to avoid disruptions.
- No Hard Tenant Limits: The architecture must not assume a fixed number of tenants or hardcoded identifiers.
Key Assumptions
- Each tenant has isolated business data, but shares core platform services (auth, messaging, workflow engine).
- Some tenants may have custom requirements (e.g., barcode formats, ERP mappings), which the system must support via extension points.
- The majority of interactions will be API-driven, either by frontend apps or external systems.
- Tenants vary in size — from startups managing a single small warehouse to enterprise clients with dozens of facilities.
Use Case / Scenario
Business Context
A SaaS company is building an inventory management platform to serve multiple clients across retail, distribution, and manufacturing sectors. These clients — the tenants — need a unified system to manage inventory across warehouses, track stock movement, and streamline order fulfillment.
Each tenant operates independently, often with unique workflows, product catalogs, and compliance requirements. For example:
- Tenant A is a DTC apparel brand with two warehouses and a Shopify integration. They need real-time inventory sync and fast fulfillment metrics.
- Tenant B is a regional wholesaler managing thousands of SKUs with expiration dates, requiring FIFO/FEFO strategies and purchase order automation.
- Tenant C is a global electronics distributor with dozens of warehouses, barcode scanning, and tight integration with NetSuite ERP and FedEx APIs.
The platform must accommodate this diversity without duplicating code or infrastructure. Each tenant gets logical data isolation, branding customization, and access to a shared ecosystem of APIs, integrations, and UI components.
Users & Roles
Users span across multiple job functions within each tenant’s organization:
- Warehouse Operators: Perform stock receiving, transfers, picking, and cycle counting via tablet or barcode scanner.
- Purchasing Agents: Create and track POs, monitor vendor SLAs, and manage reorder thresholds.
- Sales Teams: View inventory availability in real time and coordinate customer order fulfillment.
- Admins: Manage users, permissions, API keys, and custom workflows within their tenant scope.
Usage Patterns
- API Traffic: Heavy read-write traffic during business hours; real-time integrations with storefronts and ERPs drive high API concurrency.
- Warehouse Ops: Scanners and handheld devices issue rapid-fire stock movement commands with sub-second latency expectations.
- Batch Jobs: Nightly jobs to reconcile inventory, sync with external systems, and generate replenishment reports.
- Multi-region Usage: Some tenants operate in APAC, others in North America or Europe — requiring time zone handling and data locality support.
This level of multi-tenancy combined with variable workload profiles demands a design that’s both elastic and fault-tolerant, while giving tenants the feel of an isolated instance without the overhead of actual infrastructure duplication.
Need a Similar Platform?
Building a tenant-aware SaaS platform with configurable logic and industrial-grade performance isn’t trivial.
If you’re looking to design or scale a multi-tenant inventory system like this, let’s talk. We’ve built similar platforms across logistics, retail, and manufacturing — we can help you architect yours right.
High-Level Architecture
Overview
At the core of this design is a logically isolated, shared infrastructure model — tenants share compute, storage, and platform services, but access is scoped to tenant-specific data. We use AWS-native components to keep the architecture cloud-agnostic, autoscalable, and resilient.
Tenants interact with the system through a unified API gateway, which routes requests to tenant-aware services. Authentication is centralized, while business logic and data services are horizontally scalable, stateless, and event-driven where appropriate.
Database Design
Tenancy Model
This platform uses a pooled multi-tenant model with shared schema in PostgreSQL for operational data and DynamoDB for fast access to tenant-specific metadata or dynamic config. Each record in shared tables includes a tenant_id as part of its primary or composite key, ensuring logical data isolation.
This model enables horizontal scaling, simplifies operations, and reduces per-tenant infrastructure costs — while preserving tenant-level access control, backup, and auditability.
Entity-Relationship Overview
Below is a high-level conceptual ERD of core entities:
- Tenant: Stores metadata for each client (e.g., name, plan, limits).
- User: Linked to a tenant, with RBAC roles and preferences.
- Warehouse: One tenant can have many warehouses, each with zones and bins.
- Product: SKU-level entities, with attributes like barcode, weight, expiration policy.
- Inventory: Stock entries with quantity, batch ID, location (zone/bin), and audit trail.
- Purchase Order and Sales Order: Document flows tracking inbound and outbound logistics.
- Stock Movement: Logs every change in stock state — transfer, pick, receive, etc.
Here’s a simplified ER diagram:
Tenant ─────┐
├───< User
├───< Warehouse ──< Zone ──< Bin
├───< Product
├───< PurchaseOrder ──< PurchaseOrderItem
├───< SalesOrder ─────< SalesOrderItem
└───< Inventory ───────< StockMovement
Key Table Schemas (PostgreSQL)
CREATE TABLE tenant ( id UUID PRIMARY KEY, name TEXT NOT NULL, plan TEXT, created_at TIMESTAMP DEFAULT now() ); CREATE TABLE product ( id UUID PRIMARY KEY, tenant_id UUID NOT NULL, sku TEXT NOT NULL, name TEXT NOT NULL, attributes JSONB, is_active BOOLEAN DEFAULT true, FOREIGN KEY (tenant_id) REFERENCES tenant(id) ); CREATE TABLE inventory ( id UUID PRIMARY KEY, tenant_id UUID NOT NULL, product_id UUID NOT NULL, warehouse_id UUID NOT NULL, bin_id UUID, quantity INTEGER NOT NULL, batch_id TEXT, expiration_date DATE, updated_at TIMESTAMP DEFAULT now(), FOREIGN KEY (tenant_id) REFERENCES tenant(id) ); DynamoDB complements this by storing per-tenant settings, API rate limits, custom field mappings, and dynamic configuration. Sample key schema:
PK: TENANT#<tenant_id> SK: SETTINGS Multi-Tenancy Strategies
- Data Isolation: Enforced at the application and query layer — all WHERE clauses include
tenant_id. Queries are protected via an ORM or query builder enforcing scoped access. - Connection Pooling: RDS Proxy handles per-service connection scaling with IAM-based auth; no tenant-specific connections are maintained.
- Query Optimization: All frequently accessed tables have composite indexes like
(tenant_id, sku)or(tenant_id, warehouse_id).
Partitioning & Replication
PostgreSQL uses declarative partitioning (by tenant or warehouse, depending on access pattern) for high-volume tables like inventory and stock_movement. This keeps partitions small and speeds up range scans and deletes.
For analytics, Redshift or Athena can be used to run cross-tenant or per-tenant queries on warehouse-synced S3 exports.
Replication (read-replicas via RDS) supports read-scaling and analytics separation. Backups are done per-cluster, but tenant-aware exports can be triggered nightly for client-specific retention policies.
Detailed Component Design
1. Data Layer
The data access layer is tenant-aware by design. Every query includes the tenant_id filter, enforced via middleware or repository abstraction (depending on the framework).
- ORM Strategy: Postgres-backed services use Sequelize (Node.js) or SQLAlchemy (Python) with scoped sessions per tenant context.
- Validation: Schema validation (e.g., with Zod, Joi, or JSON Schema) occurs before data hits the database — important for ensuring per-tenant config isn’t violated.
- Data Access Wrapper: All queries go through a common DAL that injects tenant filters and column-level RBAC where applicable.
2. Application Layer
The application is broken into microservices by domain — e.g., inventory-service, orders-service, catalog-service, etc. Each service is stateless and independently deployable.
- Runtime: ECS Fargate or Lambda, depending on workload profile. Stateful ops (e.g., large batch sync) prefer ECS; real-time APIs lean toward Lambda.
- Framework: Fastify (Node.js) or Flask (Python) for lightweight HTTP services; NestJS or Spring Boot for structured domain-driven services.
- API Style: REST for internal services, GraphQL for tenant-facing APIs needing flexible queries.
- Security: All API requests carry a signed JWT with
tenant_idin claims. Rate limiting is applied per tenant via API Gateway usage plans.
Service Dependency Diagram
+------------------+
| API Gateway |
+--------+---------+
|
+--------------+--------------+
| |
+---------------+ +------------------+
| Auth Service | | Tenant Resolver |
+---------------+ +--------+---------+
|
+--------------------------+-----------------------------+
| | |
+--------------+ +------------------+ +-------------------+
| Catalog Svc |<----->| Inventory Svc |<------->| Order Svc |
+--------------+ +------------------+ +-------------------+
|
+--------------------+
| Stock Movement Svc |
+--------------------+
Each service communicates via HTTPS REST or lightweight gRPC, with SNS + SQS or EventBridge for async triggers like stock updates, order status changes, or low stock alerts.
3. Integration Layer
- Async Messaging: EventBridge for internal platform events (e.g., STOCK_MOVED, ORDER_PLACED). SNS/SQS for tenant-triggered workflows like webhook delivery or ERP syncs.
- External APIs: Stripe (for billing), Shopify/Magento (for inventory sync), NetSuite (for finance/inventory merge). Each is wrapped in an adapter and rate-limited by tenant.
- Webhooks: Per-tenant webhook URLs stored in config tables. Deliveries are retried with exponential backoff via SQS dead-letter queues.
4. UI Layer (Optional SaaS Frontend)
If the platform ships with a hosted UI, it’s a React/Next.js app deployed via Amplify or S3 + CloudFront, bootstrapped with the tenant’s branding at runtime.
- Auth: Uses Cognito-hosted login or embeds it into the SPA.
- RBAC: Controls which screens and fields users can access. Permissions stored in JWT claims.
- Multi-Warehouse Views: Supports toggling across facilities, zones, or bin hierarchies.
Need a Custom Architecture Like This?
If you’re designing a SaaS product with tenant-aware services, event-driven flows, or warehouse-level complexity — we can help architect, scale, or modernize your backend.
Get in touch to discuss your system design goals.
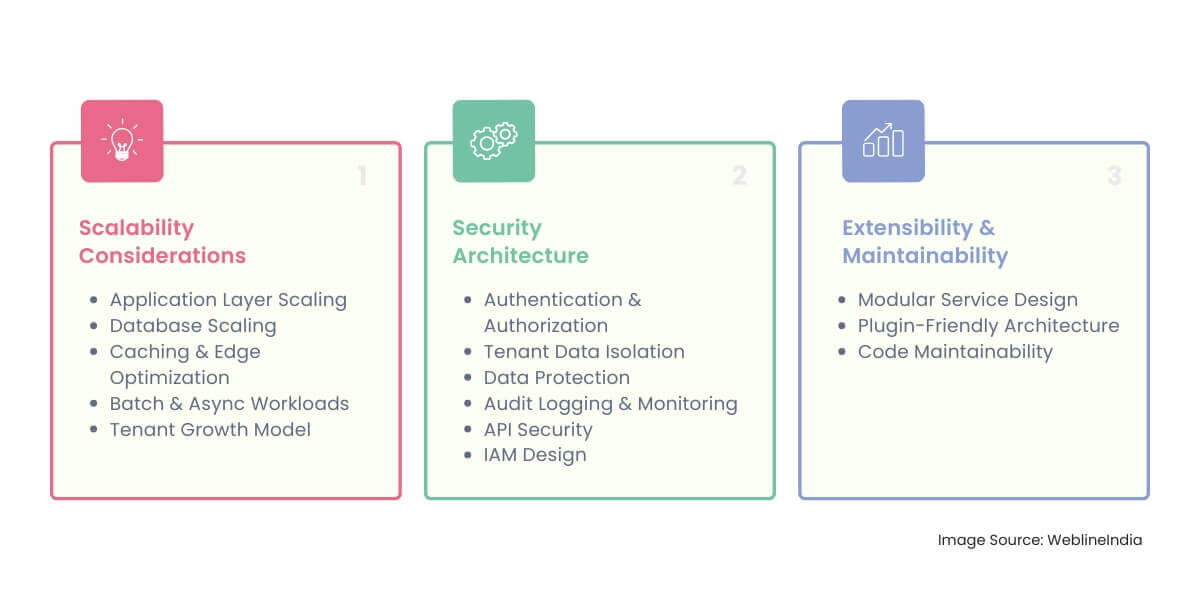
Scalability Considerations
Application Layer Scaling
- Stateless Services: All core services are stateless and horizontally scalable. ECS Fargate services auto-scale based on CPU or memory thresholds. Lambda services scale by concurrency with soft and hard tenant-specific limits.
- Per-Tenant Throttling: API Gateway enforces tenant-specific rate limits using usage plans. This protects shared infrastructure from noisy neighbors.
- Event-Driven Fanout: Inventory updates and order events are emitted to EventBridge, allowing multiple downstream services (e.g., reporting, audit logging, integrations) to consume events independently without coupling.
Database Scaling
- Read Replicas: RDS uses read replicas to offload analytics and reporting queries. Services route queries to replicas using read/write splitting logic.
- Partitioning: High-volume tables like
inventoryandstock_movementare partitioned bytenant_idorwarehouse_id, depending on access patterns. - Connection Pooling: RDS Proxy is used to manage connection limits, especially important in Lambda-based environments with rapid spiking invocations.
- Sharding (Optional): For large enterprise tenants, cross-tenant sharding may be introduced later — distributing certain high-volume tenants to dedicated schema clusters.
Caching & Edge Optimization
- Redis Caching: AWS ElastiCache (Redis) is used to cache static or frequently accessed config (e.g., product catalogs, warehouse zones). Keys are prefixed with
tenant_idto prevent collisions. - CloudFront: For UI assets and API responses that are safe to cache (e.g., product search), CloudFront improves response time and reduces origin load.
Batch & Async Workloads
- Decoupling Heavy Jobs: Inventory reconciliation, bulk uploads, and nightly exports are processed asynchronously via SQS-triggered Lambda or Fargate workers.
- Tenant-Aware Queues: High-volume tenants may be assigned dedicated queues with custom retry and concurrency settings to isolate workload impact.
Tenant Growth Model
The platform is designed to handle a mix of:
- Small Tenants: Minimal data, light traffic, single warehouse — use shared pools with basic rate limits.
- Mid-Market: Dozens of users, API integrations, multiple facilities — require tuned thresholds and isolated async workers.
- Enterprise: Heavy load, complex workflows, dedicated data volumes — candidates for isolation at DB or workload queue levels.
Elastic scaling is driven by metrics, but provisioning logic can also be driven by tenant plan tiers (e.g., free vs. premium vs. enterprise), which determine quota thresholds, resource allocation, and failover priorities.
Security Architecture
Authentication & Authorization
- Authentication: AWS Cognito handles user identity, login flows, password policies, and multi-factor auth (MFA). All JWTs include a signed
tenant_idclaim to scope requests. - Authorization: Services enforce both role-based access control (RBAC) and tenant-level policy enforcement. Admin users can configure fine-grained permissions per role (e.g., restrict PO creation or stock movements).
- Service-to-Service Auth: Backend services use IAM roles or short-lived STS tokens to authenticate inter-service calls, avoiding static credentials.
Tenant Data Isolation
- At the App Layer: Every query, mutation, and business logic path is scoped using the caller’s
tenant_id. Middleware or policy guards in the app ensure no cross-tenant access is possible, even via indirect relations. - At the DB Layer: Row-level isolation is enforced via the
tenant_idcolumn on every shared table. Additional PostgreSQL Row-Level Security (RLS) policies can be added if needed for double enforcement.
Data Protection
- Encryption in Transit: All APIs and database connections use TLS 1.2+ enforced by default.
- Encryption at Rest: RDS, S3, DynamoDB, and ElastiCache use KMS-managed encryption keys. Each tenant’s sensitive files (e.g., PO PDFs) can use separate KMS keys via S3 bucket object encryption settings.
- Secrets Management: Secrets are never hardcoded — all tokens, API keys, and credentials are stored in AWS Secrets Manager with tight IAM access controls.
Audit Logging & Monitoring
- User Activity Logs: Every user action (e.g., creating a PO, adjusting stock) is logged with
user_id,tenant_id, and timestamp in a centralized audit log table. - API Logs: CloudTrail and API Gateway access logs capture IP, auth method, and request metadata. Logs are filtered and routed to CloudWatch and S3.
- Anomaly Detection: GuardDuty and AWS Config rules monitor for suspicious activity — e.g., credential reuse, region abuse, or privilege escalation.
API Security
- Throttling: API Gateway applies per-tenant rate limiting to prevent DoS or brute-force attempts.
- Schema Validation: Requests are schema-validated at the edge to prevent malformed payloads or injection vectors.
- CORS & Headers: Only whitelisted tenant domains are allowed for cross-origin access; strict headers (HSTS, CSP, etc.) are enforced via API Gateway and CloudFront.
IAM Design
- Principle of Least Privilege: Each Lambda, ECS task, or service has a tightly scoped role — no broad access to unrelated tenants or global resources.
- Per-Tenant Isolation (Optional): For high-risk or regulated tenants, you can optionally isolate workloads in separate AWS accounts or VPCs using AWS Organizations and SCP policies.
Extensibility & Maintainability
Modular Service Design
The system follows a modular, domain-driven architecture with isolated service boundaries. Each service owns its data, its business logic, and its contracts. This makes it easy to onboard new team members, change components independently, or extend features without regressions.
- Domain Isolation: Services are grouped by functional domains (inventory, catalog, orders) — no shared business logic or cross-service DB access.
- Shared Libraries: Common utilities (logging, auth parsing, schema validation) are abstracted into shared libraries versioned per runtime (e.g.,
@inventory/common). - Well-Defined APIs: All service boundaries are exposed via OpenAPI (REST) or SDL (GraphQL). This decouples internal implementation from external contracts.
Plugin-Friendly Architecture
Tenants often need customization — whether it’s support for a regional barcode standard, ERP-specific PO formatting, or warehouse rules. Instead of hardcoding per-tenant logic, the platform exposes extension points:
- Workflow Hooks: Defined trigger points (e.g., “after stock receive”, “before PO submit”) can call tenant-registered webhooks or internal plug-in handlers.
- Custom Fields: Metadata tables allow dynamic custom fields per entity (e.g., add “color” to SKUs for fashion tenants). These are stored as JSONB with per-tenant schemas.
- Tenant Config Engine: A sidecar service or in-memory cache provides tenant-specific settings, toggle flags, and preferences injected into services at runtime.
Code Maintainability
- Linting & Formatting: All repos enforce Prettier, ESLint, or equivalent static analysis. Build pipelines fail on violations.
- Code Ownership: Each service has a dedicated team or owner. Shared code is PR-reviewed by core maintainers to avoid regressions across domains.
- Clean Code Standards: Services follow SOLID principles, single responsibility, and dependency injection wherever feasible.
Service Versioning
- Internal APIs: All internal service-to-service calls use semantically versioned endpoints (
/v1/,/v2/), with backward compatibility for at least one version. - GraphQL Schema: Uses field-level deprecation, not hard breaking changes. Clients are alerted before a field or type is removed.
- Webhook Contracts: Major version changes to webhook payloads are opt-in per tenant and versioned explicitly in delivery headers.
This approach ensures the platform can evolve — adding new features, onboarding new verticals, or adapting to emerging tech — without painful rewrites or sprawling complexity.
Designing for Long-Term Flexibility?
If you’re planning a multi-tenant platform that needs to evolve across industries, feature sets, and tenant-specific workflows — we can help you future-proof it.
Reach out for architecture guidance or hands-on support.
Performance Optimization
Database Query Tuning
- Tenant-Aware Indexing: All high-traffic tables (e.g.,
inventory,orders) are indexed using composite keys that start withtenant_id. This ensures fast access while preserving logical isolation. - Materialized Views: Frequently computed aggregates (e.g., total stock per SKU per warehouse) are precomputed and refreshed incrementally.
- Query Plan Analysis: PostgreSQL
EXPLAINoutput is used regularly in CI environments to catch regressions in query plans during schema changes.
In-Memory Caching
- Hot Lookups: Redis (via ElastiCache) caches commonly accessed items like product metadata, zone maps, or tenant settings. TTLs vary based on mutability.
- Per-Tenant Namespacing: All cache keys are prefixed with
tenant_idto prevent cross-tenant bleed. - Write-Through Strategy: For rapidly changing data (e.g., inventory quantities), Redis is updated in parallel with DB writes to keep reads blazing fast.
Async Processing & Batching
- Bulk Import Jobs: CSV or JSON imports (products, stock counts) are queued and processed in batches by workers — reducing pressure on live APIs.
- Webhook Fanout: Outbound integrations are handled asynchronously with retry logic and DLQs to avoid blocking order workflows on third-party failures.
- Batch Reconciliation: Scheduled jobs compare expected vs actual stock across warehouses and log discrepancies for user review — no runtime impact.
Rate Limiting & API Hygiene
- Per-Tenant Throttling: API Gateway usage plans enforce fair use and stop overactive tenants from degrading performance for others.
- Response Optimization: Only required fields are returned per endpoint; GraphQL allows clients to fetch minimal data payloads.
- Pagination Everywhere: All list endpoints use cursor-based pagination with consistent ordering to prevent deep scans and timeouts.
Frontend Performance Considerations
- Lazy Data Loading: Avoid eager loading of entire datasets — frontend pulls paginated data and requests details on demand.
- Static Content Caching: UI assets are versioned and cached at CloudFront edge locations. Builds are invalidated only on deploy.
- Tenant Branding at Runtime: The frontend pulls tenant-specific logos, colors, and config from a cached API endpoint to avoid per-tenant builds.
Real-Time UX Without Real-Time Cost
- Polling vs. WebSockets: Most stock and order updates are handled via short-interval polling, which scales better than persistent WebSocket infra.
- Push Notifications (Optional): For critical events (e.g., stockouts), SNS can trigger push alerts to mobile or email — offloading urgency from the UI.
The goal: fast UX, predictable workloads, no unexpected spikes — and no fire drills at 2am when a big tenant floods your system with 10K SKU syncs.
Testing Strategy
Types of Tests
- Unit Tests: All services maintain high unit test coverage, especially around business logic (e.g., inventory adjustment rules, order state transitions).
- Integration Tests: Service-to-service contracts, DB interactions, and queue/event processing are tested using real infrastructure in isolated test environments.
- End-to-End (E2E): Key tenant workflows (receive stock → allocate → fulfill order) are covered via browser automation (e.g., Playwright or Cypress).
- Regression Suites: Snapshot-based test cases protect against changes in webhook payloads, GraphQL schema, or report generation.
Tenant-Aware Testing
- Scoped Fixtures: All test data is generated with unique
tenant_ids to validate isolation across queries, APIs, and caching layers. - Multi-Tenant Scenarios: CI runs test suites across different tenant configurations — free plan, premium, multi-warehouse, etc.
- Security Boundary Tests: Negative tests validate that users can’t access or mutate data from another tenant — enforced at both service and DB layers.
CI Pipeline Testing
Each service has its own CI pipeline (GitHub Actions, GitLab CI, or CodePipeline) that includes:
- Lint → Unit → Integration → Build sequence
- Schema validation against OpenAPI/GraphQL contracts
- Docker image scanning for vulnerabilities (e.g., Trivy)
- Tagged builds trigger full E2E runs before deploy to staging
Load & Resilience Testing
- Load Tests: Simulate concurrent warehouse ops, bulk PO imports, and real-time API hits using k6 or Locust. Focus on API Gateway, DB write throughput, and queue processing.
- Chaos Testing: Inject failure into downstream systems (e.g., ERP API outage) to validate retry, fallback, and alerting behavior.
- Queue Saturation Testing: Stress SNS/SQS pipelines with thousands of concurrent events per tenant to validate decoupling and concurrency safety.
Test Environment Strategy
- Ephemeral Environments: Pull requests spin up isolated preview environments per branch with seeded tenant data. Used for demos and manual QA.
- Shared Staging: Multi-tenant staging env mirrors production, with synthetic monitoring and contract tests running continuously.
Testing in a multi-tenant system isn’t just about correctness — it’s about enforcing boundaries, validating scale assumptions, and proving that tenant diversity won’t break shared infra.
DevOps & CI/CD
CI/CD Pipeline Structure
Each microservice and the frontend (if applicable) is backed by its own CI/CD pipeline, usually implemented with GitHub Actions, GitLab CI, or AWS CodePipeline. The core steps look like this:
Git Push ↓ [CI] Lint & Static Analysis ↓ [CI] Unit & Integration Tests ↓ [CI] Docker Build & Scan ↓ [CD] Push to ECR ↓ [CD] Deploy to Staging (ephemeral env or shared) ↓ (Manual or Automated Gate) [CD] Deploy to Production (blue-green or canary)
- Artifacts: All builds generate versioned Docker images, static files (for SPA), and OpenAPI/GraphQL specs for change tracking.
- Rollback Strategy: Tagged releases are reversible within minutes using deployment version pinning or ECS task revision rollback.
Infrastructure as Code (IaC)
- Tooling: Terraform is used to provision AWS resources, organized by module (e.g.,
api_gateway.tf,rds.tf,eventbridge.tf). - State: Remote state is stored in S3 with state locking via DynamoDB. Each environment (dev, staging, prod) has isolated state files.
- Per-Tenant Overrides: For enterprise tenants requiring isolated infra, environment-specific variables (e.g., dedicated DB cluster) are injected via
terraform.tfvars.
Deployment Strategies
- Blue-Green Deployments: Default method for backend services. New versions are deployed to a staging target group and traffic is cut over only after health checks pass.
- Canary Releases: Used for high-impact or experimental changes — e.g., new inventory reconciliation logic — deployed to a subset of tenants first.
- Feature Flags: Feature rollout is tenant-aware using LaunchDarkly or a custom toggle engine. Enables controlled rollouts, A/B tests, or plan-based feature gating.
Secrets & Configuration Management
- Secrets: Managed with AWS Secrets Manager. Short-lived tokens (e.g., STS) are generated at runtime where possible to avoid long-term secrets.
- Config: Per-tenant config is stored in DynamoDB and cached in Redis at runtime. Environment-level config is injected via Parameter Store or ECS task definitions.
Developer Experience
- Local Dev: Docker Compose files mimic core services (API, DB, queues) with seeded test tenants. Frontend autoconfigures based on local or remote tenant settings.
- Tooling: CLI tools allow engineers to spin up test tenants, simulate events, or seed data — reducing manual test prep time.
- Preview Environments: Every PR deploys to a short-lived environment accessible via a unique URL, with pre-seeded tenant data. Used for design reviews and QA.
The platform’s DevOps pipeline is designed to prioritize velocity, safety, and rollback simplicity. Engineers ship fast, without breaking tenants or waking up at 3am.
If you’re scaling a multi-tenant platform and need bulletproof CI/CD, zero-downtime deployments, and tenant-aware infra automation – let’s talk.
We’ve helped teams go from fragile scripts to production-grade pipelines with confidence.
Monitoring & Observability
Logging
- Structured Logging: All services emit structured JSON logs with standard fields like
tenant_id,request_id,service, andseverity. This enables tenant-level filtering and fast debugging. - Centralized Aggregation: Logs from ECS, Lambda, and API Gateway are streamed to CloudWatch Logs and optionally forwarded to an ELK stack (ElasticSearch/Kibana) or Datadog for long-term storage and visualization.
- PII Scrubbing: Middleware sanitizes sensitive fields before logging (e.g., user emails, addresses, payment data) — enforced by a shared logging wrapper.
Metrics
- Application Metrics: Custom business metrics like “orders per tenant per hour”, “stock movement latency”, and “failed PO syncs” are exposed via embedded Prometheus exporters or CloudWatch Embedded Metric Format (EMF).
- Infrastructure Metrics: All AWS-managed services (RDS, ECS, SQS) emit native CloudWatch metrics. Alerts are defined for thresholds on CPU, memory, IOPS, and queue length.
- Tenant Isolation Signals: Metrics are tagged with
tenant_idortenant_planto detect noisy neighbors, saturation patterns, or degraded SLAs at a granular level.
Tracing
- Distributed Tracing: AWS X-Ray (or Datadog APM, if preferred) traces requests end-to-end across services, queues, and DB calls. Each trace includes
tenant_idanduser_idin annotations for traceability. - Correlation IDs: A
x-request-idheader is passed through all service hops, making it easy to track a request’s lifecycle across logs and traces.
Dashboards
- Global Dashboards: Show system-wide health, API latency percentiles, queue backlogs, DB throughput, and error rates.
- Per-Tenant Dashboards: Optionally generate tenant-specific views (especially for enterprise clients) that highlight their usage patterns, error volume, and system performance.
Alerting
- Service Alerts: CloudWatch Alarms or Datadog Monitors trigger on high error rates, timeouts, or resource saturation. Alerts are routed to Slack, PagerDuty, or OpsGenie channels.
- SLO Breach Detection: Predefined service-level objectives (e.g.,
99.9% order API availability) are tracked and reported. Breaches generate tickets or postmortem triggers. - Anomaly Detection: CloudWatch anomaly detection monitors usage curves and flags unusual spikes in traffic, errors, or resource consumption per tenant.
Health Checks & Uptime Monitoring
- Liveness & Readiness Probes: ECS services expose
/healthzendpoints for container-level health management. Load balancers and deployment strategies rely on these for safe rollouts. - Third-Party Monitoring: Uptime Robot, Pingdom, or StatusCake monitor public endpoints, including tenant-branded subdomains and APIs.
- Status Pages: Public status page (e.g., hosted on Statuspage.io) displays real-time uptime, incidents, and system metrics — useful for enterprise transparency.
In a shared multi-tenant system, observability isn’t optional. It’s your only defense against latent bugs, cross-tenant regressions, and silent degradation.
Trade-offs & Design Decisions
Shared Schema vs. Isolated Schema
- Decision: Use a shared schema, single database model with
tenant_idenforced at the application and query layer. - Why: This enables simpler schema management, avoids duplicating migrations, and makes cross-tenant analytics easier. It’s cost-efficient and operationally lean at scale.
- Trade-offs: Requires extreme discipline in query scoping and tenant filtering. Mistakes can lead to data leaks. Heavy tenants may still require performance isolation (handled via partitioning or replicas).
PostgreSQL + DynamoDB Hybrid
- Decision: Use PostgreSQL for relational consistency and complex joins; DynamoDB for high-speed metadata/config access and distributed tenant settings.
- Why: Many entities (e.g., SKUs, orders) demand relational logic. But tenant-specific settings, toggle flags, and user preferences are better served by key-value reads.
- Trade-offs: Operational overhead in managing two persistence engines. Risk of desync if write orchestration is sloppy.
Event-Driven Architecture
- Decision: Use EventBridge + SNS/SQS for decoupled, async processing of events like inventory changes, PO receipts, and order webhooks.
- Why: Keeps services loosely coupled. Enables independent retries, horizontal scaling of consumers, and easier extension via event listeners.
- Trade-offs: Eventual consistency. Observability becomes harder — need distributed tracing and correlation IDs to debug multi-hop flows.
Multi-Tenant vs. Per-Tenant Isolation
- Decision: All tenants share infra by default; high-throughput tenants can be optionally isolated at the database or queue layer.
- Why: This balances cost and simplicity. Most tenants don’t justify their own infra. Enterprise tenants that do can still be carved out via config-driven overrides.
- Trade-offs: Adds complexity in provisioning and deploy logic. Not all services are aware of isolation — needs better tooling to handle exceptions cleanly.
GraphQL vs REST
- Decision: Use REST for internal service calls; GraphQL for external APIs consumed by frontends or tenant systems.
- Why: REST simplifies service decomposition and documentation. GraphQL gives tenants flexibility in querying complex data shapes (e.g., nested stock views).
- Trade-offs: GraphQL adds learning curve and complexity around permissions, pagination, and schema evolution. Requires gateway orchestration and strict field-level guards.
Plugin Hooks vs Hardcoded Logic
- Decision: Add webhook/plugin hook support to key workflows instead of hardcoding per-tenant logic.
- Why: Gives flexibility without creating if-else ladders per tenant. Keeps core clean and allows custom logic to evolve independently.
- Trade-offs: Plugins can fail or introduce latency. You need guardrails — timeout limits, retries, and safe fallback logic.
What Was Deliberately Avoided
- Per-Tenant DBs by Default: Too costly, slow to provision, hard to maintain at scale. Reserved for VIP clients only.
- Real-Time WebSockets: Deferred for v2 — polling and push notifications cover most needs without requiring persistent socket infra and scaling complexity.
- Hard Multi-Region: Started with single-region HA + backups. Multi-region writes and data residency routing require stronger tenant segmentation — deferred until needed.
Every decision was made with scale, team velocity, and tenant diversity in mind. The system is intentionally flexible but not overengineered.
What This Architecture Gets Right
Designing a multi-tenant inventory management platform isn’t just about ticking boxes on AWS service usage — it’s about orchestrating scale, flexibility, and safety for a diverse set of customers, all running through shared infrastructure.
This architecture hits the balance between cost efficiency and tenant isolation. It allows small and mid-market clients to coexist with enterprise giants, without friction. It provides structure where needed — service boundaries, RBAC, event contracts — but keeps room for organic growth via plugins, config overrides, and async workers.
Some of the strongest aspects of the design:
- Strict, enforced tenant data isolation at every layer — from database to API to logs.
- Robust event-driven backbone for extensibility and decoupling.
- Modular service architecture with clean deployment boundaries and versioning.
- Flexible tenancy model — shared by default, isolated when needed.
- Developer-first CI/CD pipeline with test environments and feature flags.
Of course, no system is static. What’s solid today might break under a 10x scale or new use case tomorrow. Areas to keep an eye on as you grow:
- Event bloat: Too many listeners or unclear contracts will eventually lead to drift or unintended coupling.
- Analytics scale: More tenants means more query noise — segment analytical workloads from operational ones early.
- Global expansion: You’ll eventually need to deal with multi-region, latency-sensitive tenants and data sovereignty laws.
The foundation, though? Rock solid. This architecture scales linearly, supports agility, and lets your team build confidently — while giving tenants the feel of a system built just for them.
Need Help Architecting Something Similar?
Whether you’re launching a new SaaS product, modernizing a legacy monolith, or scaling to support thousands of tenants — we can help design it right.
Reach out to discuss about multi-tenancy, AWS and clean architecture that lasts.
Frequently Asked Questions (FAQs)
1. How to build multi-tenant SaaS?
To build a multi-tenant SaaS platform, start with a clear tenancy model (shared DB, isolated DB, or hybrid), implement tenant-aware authentication and authorization, and design your services to enforce strict tenant boundaries. Use infrastructure like AWS Cognito, API Gateway, and IAM for identity control, and partition data using a tenant_id across your schema. A well-structured, modular architecture ensures scalability and tenant-level extensibility.
2. How do I create a multi-tenant database?
A multi-tenant database can be created using one of three patterns: shared schema (all tenants in the same tables, scoped by tenant_id), schema-per-tenant (each tenant has their own schema), or database-per-tenant. For SaaS at scale, the shared schema model is often preferred for cost-efficiency and operational simplicity. Use composite indexes, row-level security (RLS), and scoped query access to enforce tenant isolation.
3. How to create multitenant SaaS based application in microservice?
To create a multi-tenant SaaS application using microservices, define clear service boundaries (inventory, orders, billing), make services stateless, and enforce tenant isolation at the data and service layer. Each microservice should validate tenant_id from the request context and avoid cross-tenant access. Use a shared auth provider (e.g., AWS Cognito), tenant-aware routing, and async messaging (like SNS/SQS) to decouple flows.
4. What are the 4 types of inventory management system?
The four main types of inventory management systems are: (1) Perpetual Inventory, which updates in real-time; (2) Periodic Inventory, updated at intervals; (3) Barcode-based Systems, used in retail and warehousing; and (4) RFID-based Systems, which use tags and sensors. Modern SaaS platforms often blend multiple types, depending on industry needs.
5. Can you build SaaS without coding?
Yes, it’s possible to build a basic SaaS product without coding using no-code platforms like Bubble, Glide, or OutSystems. However, for scalable, secure, multi-tenant SaaS (especially involving inventory, ERP, or logistics workflows), custom code is essential. No-code is great for MVPs, but production-grade systems require architectural control.
6. What is the best architecture for multi-tenant SaaS on AWS?
The best AWS architecture for multi-tenant SaaS includes a combination of API Gateway, AWS Cognito, ECS/Lambda services, RDS for structured data, DynamoDB for metadata, and S3 for object storage — all scoped per tenant. Use EventBridge and SNS/SQS for async processing and CloudWatch for observability.
7. How do you isolate tenant data in a shared database?
Tenant data is isolated in a shared schema using a tenant_id column on every row, enforced through application-level guards, database indexes, and optionally PostgreSQL row-level security (RLS). APIs and services must always scope queries to the authenticated tenant.
8. How do you handle tenant-specific configuration in SaaS?
Store tenant-specific configurations (like workflows, UI flags, thresholds) in a metadata store such as DynamoDB or PostgreSQL JSONB. Use a config service or in-memory cache to inject this at runtime across services. This allows per-tenant customizations without forking code.
9. What CI/CD pipeline is best for multi-tenant platforms?
The best CI/CD pipeline for multi-tenant SaaS includes isolated build/test workflows per service, tenant-aware test environments, canary deployments, and feature flags. Tools like GitHub Actions + Terraform + ECR + ECS provide a robust foundation.
10. How do you scale a multi-tenant SaaS application?
Scale horizontally by keeping services stateless, databases partitioned, and workloads decoupled via event-driven patterns. Use per-tenant rate limits, caching layers, and read replicas. For heavy tenants, isolate at the DB or queue level.
Testimonials: Hear It Straight From Our Global Clients
Our development processes delivers dynamic solutions to tackle business challenges, optimize costs, and drive digital transformation. Expert-backed solutions enhance client retention and online presence, with proven success stories highlighting real-world problem-solving through innovative applications. Our esteemed Worldwide clients just experienced it.
Awards and Recognitions
While delighted clients are our greatest motivation, industry recognition holds significant value. WeblineIndia has consistently led in technology, with awards and accolades reaffirming our excellence.
OA500 Global Outsourcing Firms 2025, by Outsource Accelerator

Top Software Development Company, by GoodFirms

BEST FINTECH PRODUCT SOLUTION COMPANY - 2022, by GESIA

Awarded as - TOP APP DEVELOPMENT COMPANY IN INDIA of the YEAR 2020, by SoftwareSuggest